Email encryption is something that everyone should know about, whether you are using email communication for your personal purposes or transferring sensitive information within an enterprise organization.
In this article, we explain several types of encryption, from basic to advanced ones, and also provide instructions on how to implement them.
How email encryption works
Encryption is a method to cipher your message and its content in a way that it can’t be interpreted by unintended recipients.
There are two common email encryption methods:
- Encryption in transit (you probably know it as TLS/SSL/STARTTLS)
- End-to-end email encryption, or public key encryption (which is obviously a more advanced option)
Now let’s review each of them in detail.
TLS encryption
TLS stands for Transport Layer Security and, as its name suggests, it protects emails during transportation from a sender to a receiver. It is a reliable method used by default in many email clients, such as Gmail and Yahoo. Why do we say that this is just a basic encryption? Because TLS secures the message transition channel, not the email itself. This way, the email content becomes insecure as soon as it reaches the recipient.
How does it work and how do you enable it?
To establish TLS secure connection, STARTTLS is used. It is a command that instructs the email server to switch to a secure connection via TLS or SSL (SSL, Secure Socket Layer, is a TLS predecessor). It is compatible with SMTP and IMAP protocols.
To enable STARTTLS for your email client or server, you usually need to set the proper configuration in its settings. Another thing to remember is the dependency on ports — port 465 is mainly used for Implicit SSL/TLS, while 587 is more common for Explicit SSL/TLS. What’s the difference?
- With Implicit, or Forced, SSL/TLS, a sender’s server sends a request to a recipient’s server for establishing a secure connection. If the recipient’s server doesn’t support TLS and the exchange of the encrypted keys can’t be performed, data transition won’t be allowed. This means that the email won’t be sent at all.
- With Explicit, or Opportunistic, SSL/TLS, a sender’s server also sends a request to a recipient’s server for establishing a secure connection. However, in this case, if the recipient’s server is not compatible and the secure connection can’t be established, data transition will happen anyway, but via an unencrypted channel.
Read our STARTTLS vs SSL vs TLS blog post for more details on the email encryption in transit.
End-to-end encryption
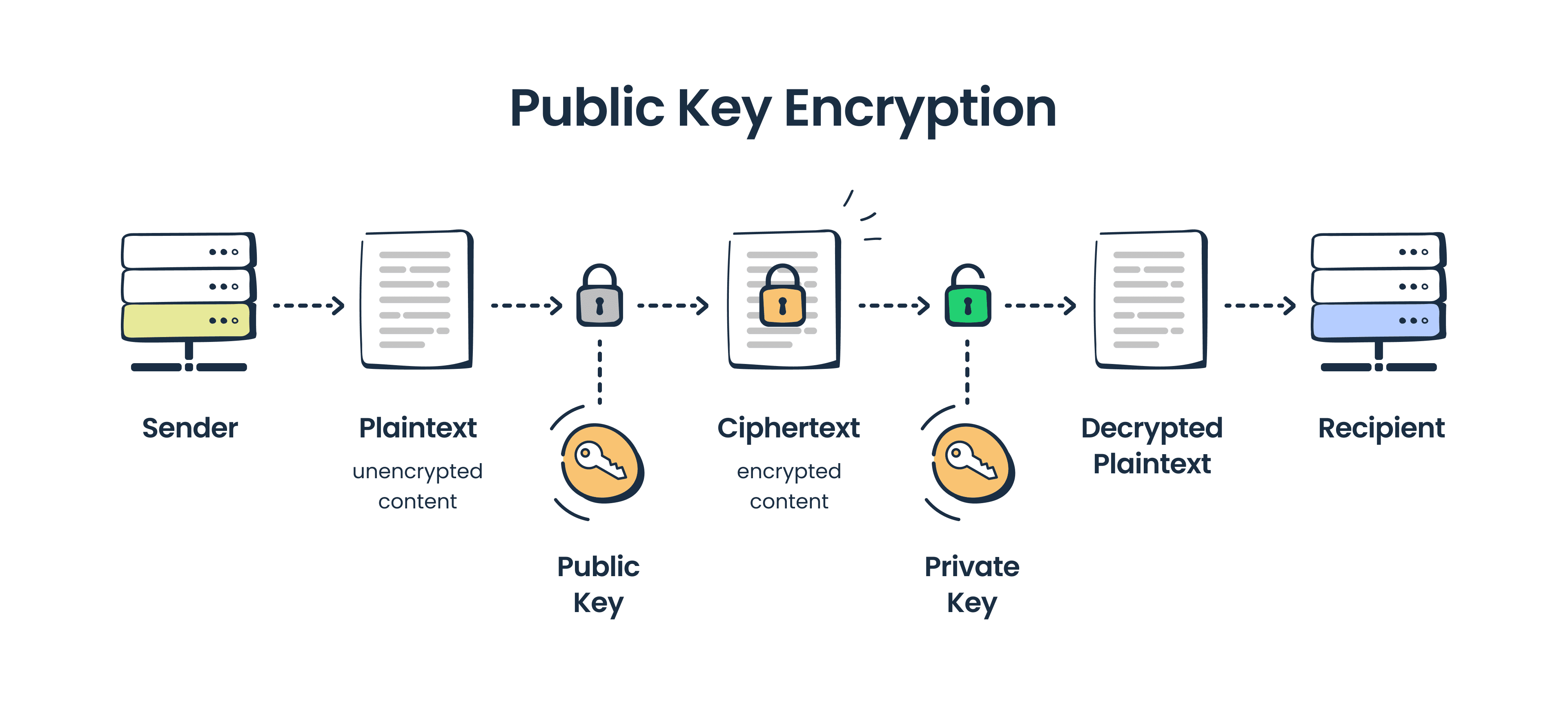
When sending sensitive data, following different business purposes, you need to be sure that your emails are secure within the whole cycle of their transmission from sender to recipient. This can be implemented with the help of end-to-end email encryption. This type of encryption uses public keys to protect emails and their content, including attachments. When encrypted, the message content is ciphered, or put simply, converted into an unreadable format. Only the intended recipient who has a special key can decipher it and understand its content.
End-to-end encryption utilizes a pair of digital keys — a public and a private one. Your public key is connected to your email address and is accessible to other people so that they can find you and send you encrypted emails. This recipient’s public key is used to encrypt a message. To decrypt it, you, as the recipient, need to use your private key, which is stored safely and is available only for you, its owner.
There are a few types of solutions and protocols that ensure end-to-end email encryption.
S/MIME
S/MIME stands for Secure/Multipurpose Internet Mail Extensions. It provides so-called asymmetric encryption implemented with S/MIME certificates. S/MIME allows you to encrypt and digitally sign emails so that only dedicated recipients can decrypt and access their content. S/MIME uses a set of public and private keys that have to match:
- The public key is used for authentication. It is sent with each message to identify the sender.
- The private key is used for decryption and also for generating a digital signature.
To send someone a S/MIME encrypted email you have to receive their digital signature first.
Also, you need to obtain S/MIME certificates from the certified authorities — S/MIME is mostly used inside organizations, so business email providers usually have this encryption option included. Otherwise, there are third-party authorities that offer S/MIME certificates.
Gmail and Outlook have S/MIME encryption available on business subscription plans, while it is included for all users on iOS devices. We will talk more about sending encrypted messages in different email clients later in this article.
OpenPGP
OpenPGP is another common email encryption standard. Its history starts in 1991 when Pretty Good Privacy (PGP) software was released. It was created to encrypt not only emails but also texts, files, and whole directories. PGP was the first public-key cryptographic program that became commonly accessible. The first version was available through a public FTTP and then it was spread over the internet. Phil Zimmerman, the creator of PGP, even was under investigation by the US Government (because of the cryptographic software being exported out of the US).
Now PGP is owned by the American software company NortonLifeLock Inc., formerly known as Symantec, and the OpenPGP standard is supported by numerous software applications. GNU Privacy Guard (GPG), also known as GnuPG or GPG, is the most widely used tool as it comes installed on the majority of GNU/Linux operating systems.
GPG is a command-line tool that you can easily integrate with other apps. However, there are a bunch of wrappers around GPG including graphical user interface, mail user agents, frontends for scripting, and more. You can find the whole list on the GPG official page.
For Windows users, there is a Gpg4win version with a context menu tool, a crypto manager, and an Outlook plugin.
The list of tools that support the OpenPGP standard is available on its official website.
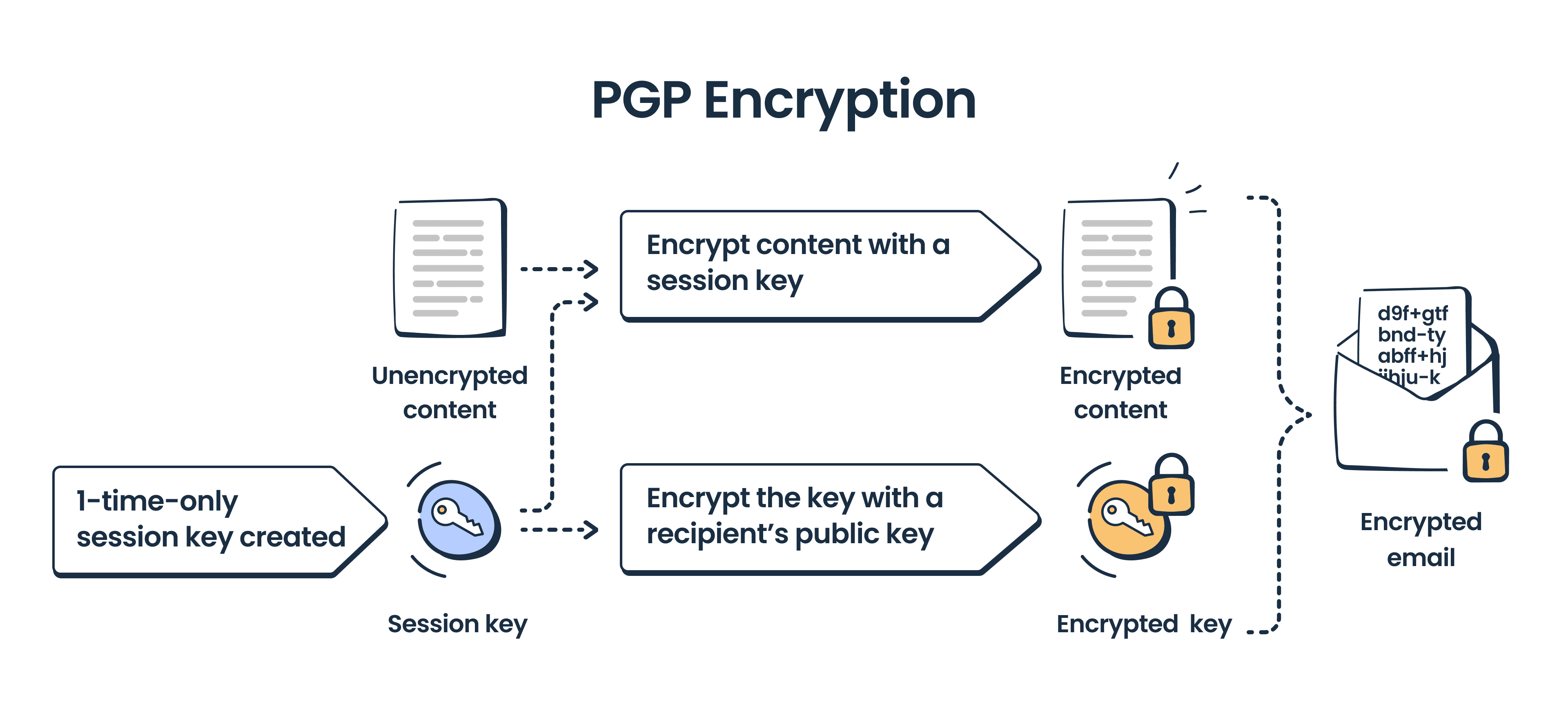
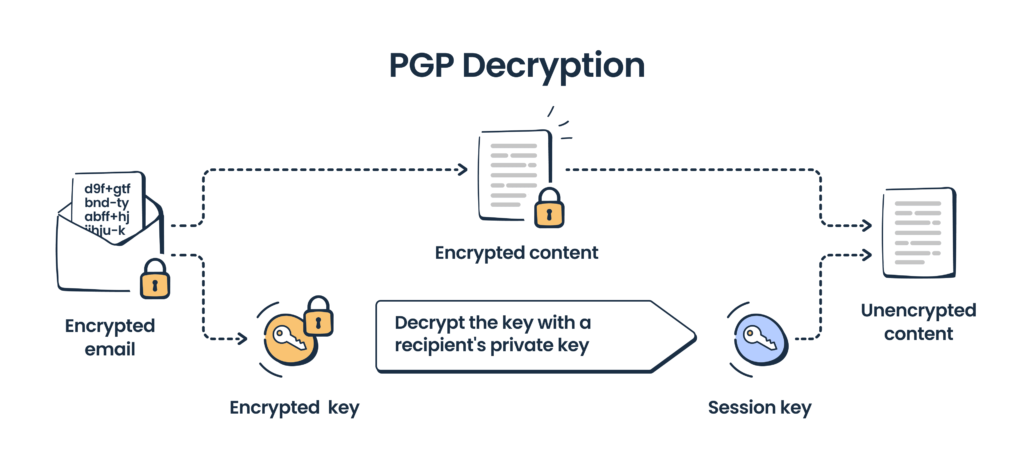
OpenPGP encryption is based on a set of private and public keys, similar to S/MIME. The encryption program, let’s say PGP, also features a digital signature. The difference is that PGP uses symmetric encryption, which means that one and the same key is used to encrypt and decrypt a message. However, this session key is encrypted with the recipient’s public key.
Symmetric encryption is significantly faster than asymmetric, but without this extra key encryption, it won’t be that secure.
OpenPGP encryption is much more common for personal email messaging.
Bitmessage
Here is one more interesting, but less popular solution: Bitmessage. It is a peer-to-peer communication protocol for sending encrypted messages. Bitmessage is designed on the principles of Bitcoin, and it is also decentralized. This means that Bitmessage doesn’t utilize and doesn’t depend on central servers or certificate authorities.
Bitmessage also uses a set of corresponding public and private keys. It encrypts emails with the recipient’s public key but its main difference is that it doesn’t expose any information about the message sender and its recipients. Therefore, an anonymized recipient means that every message is delivered to each member of the Bitmessage network. Only the intended recipients are able to decrypt it with the matching private key. Such a method prevents spoofing though.
To use Bitmessage, you need to install a bitmessage client or you can refer to the project’s page on GitHub.
How to send secure emails
We have reviewed how email encryption works and examined a few email encryption methods with samples of their implementation. Now let’s focus on ways of sending secure emails in different environments.
In general, there are three main approaches to sending encrypted emails:
- Programmatic — we touched on it in the OpenPGP section
- Switching to an encrypted email provider
- Sending with your regular email client, but setting the built-in email encryption option or using a third-party plugin/solution
Let’s review the second and third in more detail.
Encrypted email providers
If you are thinking about setting a new infrastructure, or are just ready to start from scratch and switch to a new email provider for a certain type of communication, you have a wide range of tools to choose from. Check out our article on email encryption software for a more detailed comparison. Here we will list just a few popular and reliable options.
The first solution on our list is ProtonMail, which is an email client available as a web and mobile app. It features end-to-end encryption, a user-friendly interface, and a generous free plan to start with.
Other similar email clients are Tutanota and Hushmail.
If your business requires compliance with particular standards, such as HIPAA for the medical industry, you should search for a dedicated solution. We have written about HIPAA-compliant email providers earlier as well. In this category, you will find specialized healthcare software, such as Paubox, and other business solutions, such as Virtru, certified for use in healthcare communications.
Common email clients
What if you need to send encrypted emails using your regular email client, such as Gmail or Outlook? All of them feature email encryption, but with some limits. By default, the majority of email clients ensure TLS encryption. If you need end-to-end encryption, you should take care of the additional configuration.
In general, Outlook, Gmail, and Apple Mail support S/MIME and have it included (with some restrictions), while Yahoo doesn’t have any end-to-end encryption included. We would recommend using the following approach: if email privacy is important for your type of communication, use the end-to-end encryption option available for your email client. If it’s not supported or not available, use a professional plugin suitable for your tasks and budget.
Email encryption in Gmail
You have an option to encrypt your Gmail messages with S/MIME standard; however, it is available only for Enterprise, Education Fundamentals, and Plus editions. If you are using one of these, you can configure S/MIME in the admin console and then upload certificates obtained from one of the trusted authorities (see the full list in the Google documentation). Note that both sender and recipient must enable S/MIME and exchange certificates to be able to exchange encrypted messages.
If you are using Gmail for personal purposes, but still need to send encrypted messages, or prefer other encryption standards, we recommend picking a third-party plugin, such as Virtru or FlowCrypt.
You might have heard of the Gmail confidential mode. Indeed, it protects your messages from forwarding, copying, downloading, etc., but, in fact, it’s not secure. Confidential Gmail messages are not encrypted with an end-to-end encryption protocol and still are stored on Google servers. Therefore, to encrypt email attachments, it’s better to install a plugin that provides end-to-end encryption.
Email encryption in Outlook
There are three main options for Outlook encryption: S/MIME, Microsoft 365 Message Encryption (OME), or a third-party service.
S/MIME encryption is available for all Outlook users that have Outlook 2010 or later versions (but is not supported in Outlook on the web on Mac, iOS, Android, or other non-Windows devices). To enable S/MIME, you need to configure certificates first. They can be obtained from the Windows-based Certification Authority or a third-party authority.
Microsoft 365 Message Encryption (OME) is available for Microsoft 365 Enterprise E3 users. It combines email encryption and rights management capabilities by Azure Information Protection.
Email encryption on Mac and iOS devices
As we have already mentioned, AppleMail, the default email app on macOS and iOS devices, features built-in S/MIME encryption.
You don’t need to load any additional certificates, just enable Encryption in the advanced settings. If both you and your email recipient belong to the same Exchange environment, you can start messaging right away. If you are not inside the same Exchange environment, then you need to install encryption certificates for this recipient. This is available inside the Apple Mail functionality.
Alternatively, you can always use extensions for OpenPGP encryption or switch to a secure email client, such as Canary Mail.
Final words
Obviously, you want to keep your email communication safe and inaccessible to unintended recipients. By default, the majority of your emails are protected with TLS encryption, even newsletters from your favorite shop or magazine.
For corporate communications or sending sensitive personal information, you need to take care of the end-to-end encryption to keep your email content with attachments inaccessible to unintended recipients. Note that you need the recipient’s consent for sending them emails encrypted with public keys as you need to exchange your digital keys first.
Data protection is of high importance and attention these days, which means that you have a wide set of options for sending and receiving encrypted emails. We hope that having read this article you can easily choose the method and the tool that matches your needs.